Today I run into domain abuse while working on a WordPress project due to a typo in the TLD. A foreign server happily served me the requested files but with spiced content. This looked unsuspicious at first glance.
Now this is something that doesn’t happen every day [to me]. I haven’t touched PHP and WordPress in years so I don’t have a workflow established for this any more. Today I got the job to upgrade some legacy system. So I checked out the project from git, configured some dnsmasq magic and launched a local PHP development server and browser.
I was astonished when the project came up in the zero profile development chrome and the first link I clicked opened a new tab presenting me with some scam ringing all alarm bells. I’m on localhost! And Linux! What happened? Do we have an infected project in our git repository? So I started digging.

Wait, this doesn’t look right. Looks like I made a typo replacing the WordPress WP_HOME and WP_SITEURL in our local wp-config and got a doubled dot de. That’s not going to localhost but it’s still loading JavaScript files. No file came back with 404 – Not Found error so at first glance nothing suspicous happened beside the CSS looking weird. Most files were empty but with some exception – as you can see.

So I run that IP against the IP Abuse DB and it checked out with various reports including a “took over my blog” report. Yeah, I guess that happens when you’re going to login to your blog. This IP ships any file you request back to you but with it’s own flavoured JavaScript. That’s what happens when you do a typo and someone else is just waiting for this. And it happened to my dev setup since I made a search and replace without enough caffeine in my blood to spot the typo and without bothering to set up SSL and CORS for developing.

So yeah.. you can throw any domain at this. It will happily serve malware, or spam or whatever it’s up to today. It’s just waiting for a typing error.
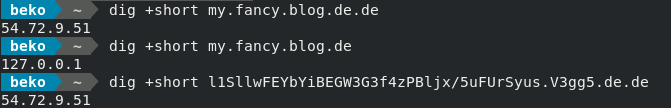
There’s a lesson here. Watch careful what domain you really use. Don’t be lazy and make use of SSL/CORS even in development. I can’t help me from having some respect for this idea and there are probably others doing the same.

